Through the Lens of Six Months: Unveiling the Citrix Bleed Patching and Exploitation Patterns
■Summary
I conducted a retrospective study on the vulnerability CVE-2023-4966, commonly known as Citrix Bleed, which allows attackers to easily bypass authentication in Citrix's Citrix ADC and Citrix Gateway products, over the course of six months. Initially exploited by some attackers as a zero-day in August 2023, a patch was released on October 10, followed by the publication of a PoC in late October, after which various attackers exploited the vulnerability. This research was conducted based on publicly available information to understand how the vulnerability was addressed and exploited.
Normally, articles on this media are written in Japanese, but this article is written in English to reach a wider audience.
通常、当メディアの記事は日本語で書かれていますが、この記事はより多くの読者に情報を届けるため英語で書かれています。
■Regarding the status of patch application
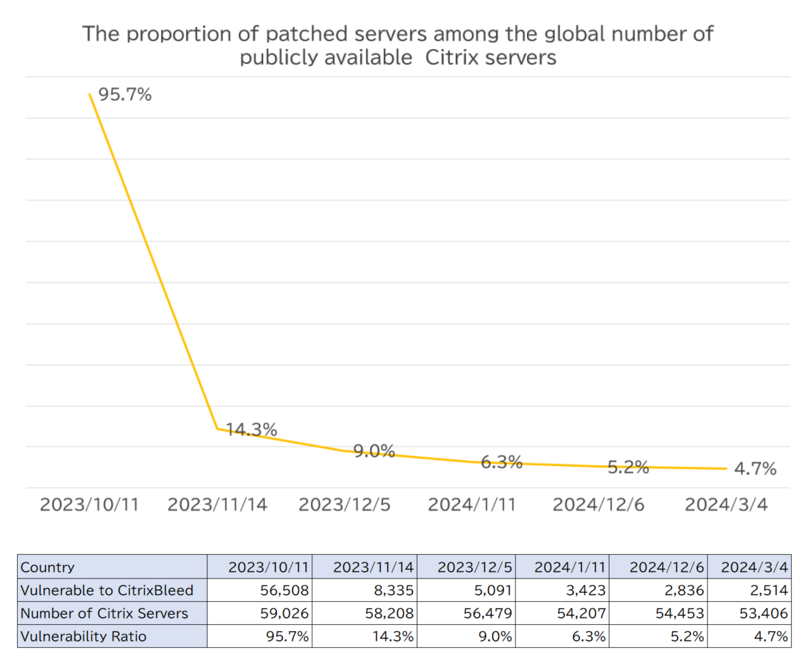
Regarding the patch application status, Users of this products are often large corporations with good management practices, which may explain why the response to this vulnerability was considerably faster than the response to other vulnerabilities. Within one month of the patch release, about 50,000 servers, which corresponds to 85% of the approximately 58,000 servers publicly available worldwide, were addressed.
*From my experience, the speed of patch application clearly varies by device. For example, Ivanti VPN tends to be slightly slower than Citrix, and FortiGate is significantly slower. I believe this reflects the size of the companies using the devices and their security literacy. The more a small organization uses it, the duller their sensitivity to vulnerability information, and the slower their response. It may be effective to adopt a different vulnerability communication strategy for each device, considering the nature of its users.
However, after that initial period, progress slowed, and the number of unpatched devices has not significantly decreased in the last three months. As of early March, it is estimated that there are still about 2,500 servers globally that have not been patched (This figure includes a small percentage of honeypot servers and those to which some form of mitigation has been applied). Since there are 53,406 Citrix servers exposed to the internet, 4.7% of them are in a vulnerable state.
When it comes to drawing such a trend line, it is impossible to completely eradicate vulnerable servers. This is why incidents caused by a certain vulnerability do not cease even years after its discovery, and why damages continue to be reported over many years. Although they represent a small percentage numerically, more than 2,000 servers are vulnerable. I believe that encouraging the application of patches to such servers (The last mile in patch application) is a global challenge.
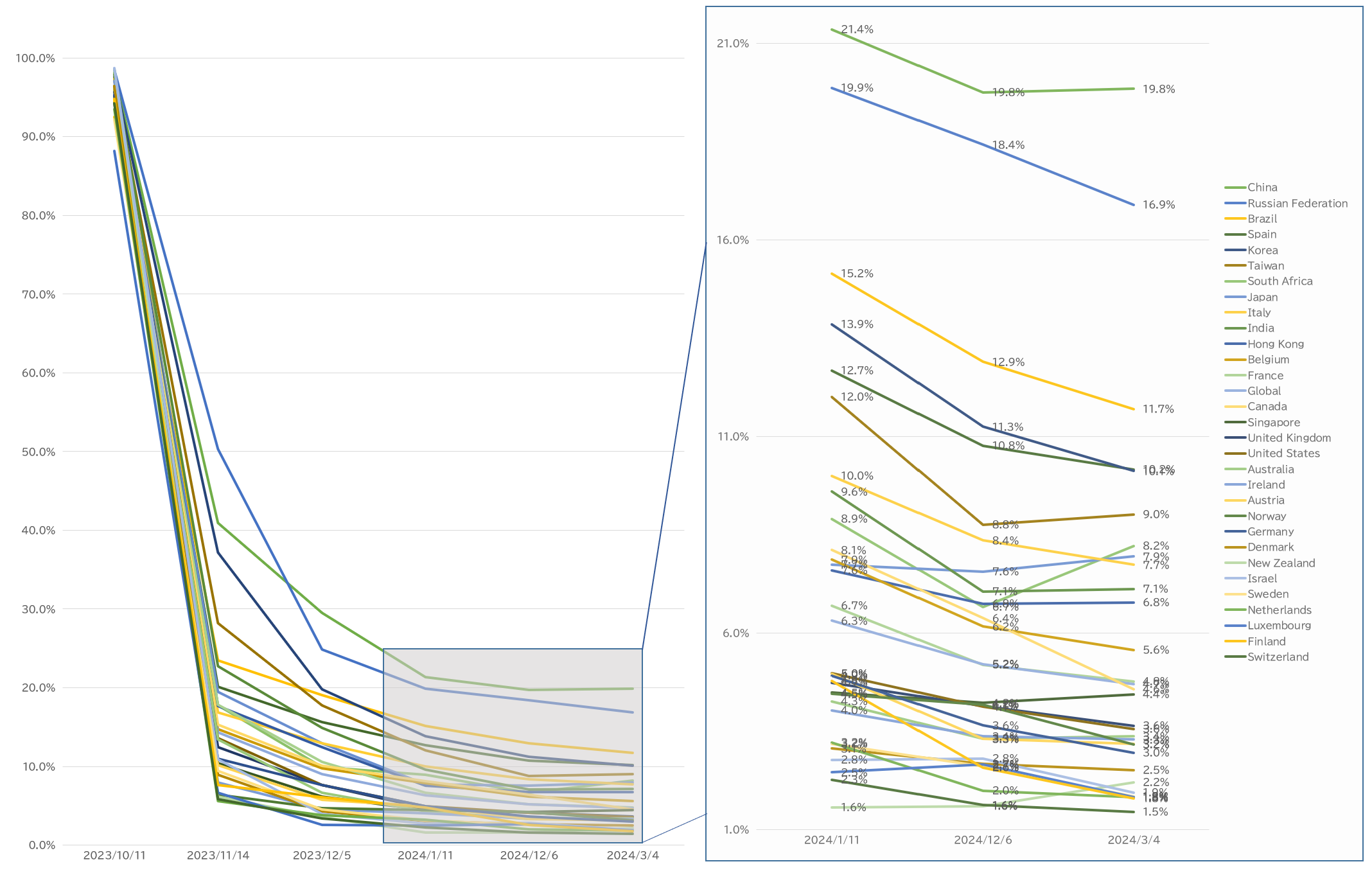
The data by country is as follows: The top 30 countries with the highest number of Citrix servers are extracted, and the proportion of servers in those countries that have not been patched is graphed. Furthermore, the countries are sorted in order of poorest performance.
As with other vulnerabilities, the trend shows that countries with poor patch application rates often include those in the Asian region.
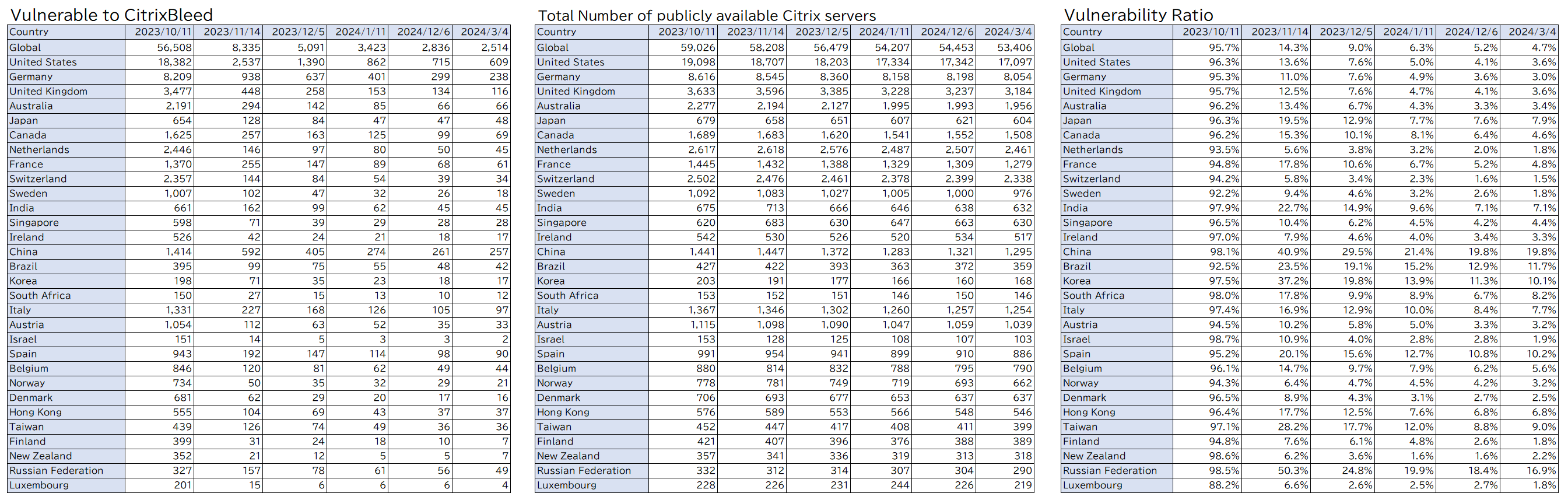
The detailed data by country is as follows.
■Method for investigating public servers
As I presented at JSAC2023( International security conference held in Japan ) in January 2023, I have been investigating the public servers of companies leaked by ransom actors and researching what products attackers exploit. This research method has previously revealed various attack trends, such as the exploitation of VMware Horizon by Pandora , QNAP NAS by DeadBolt , Cisco ASA by Akira , MOVEit by Cl0P and more.
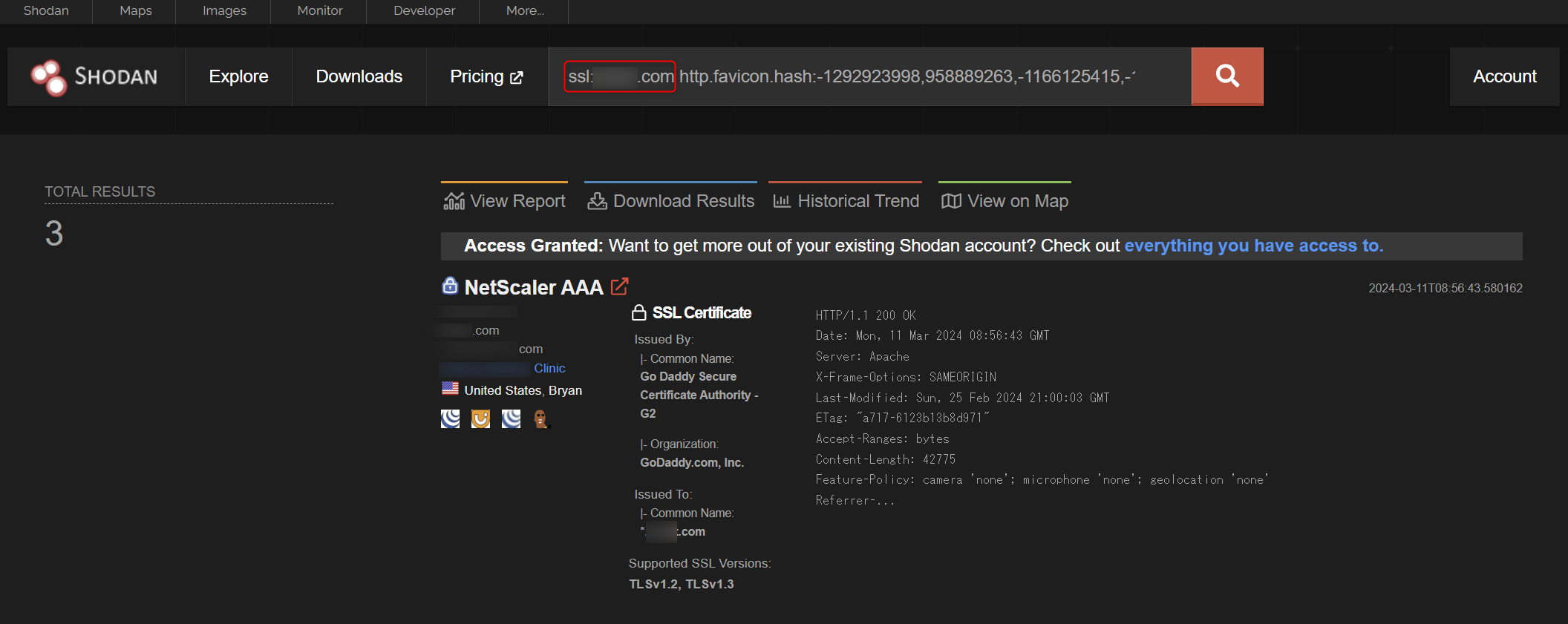
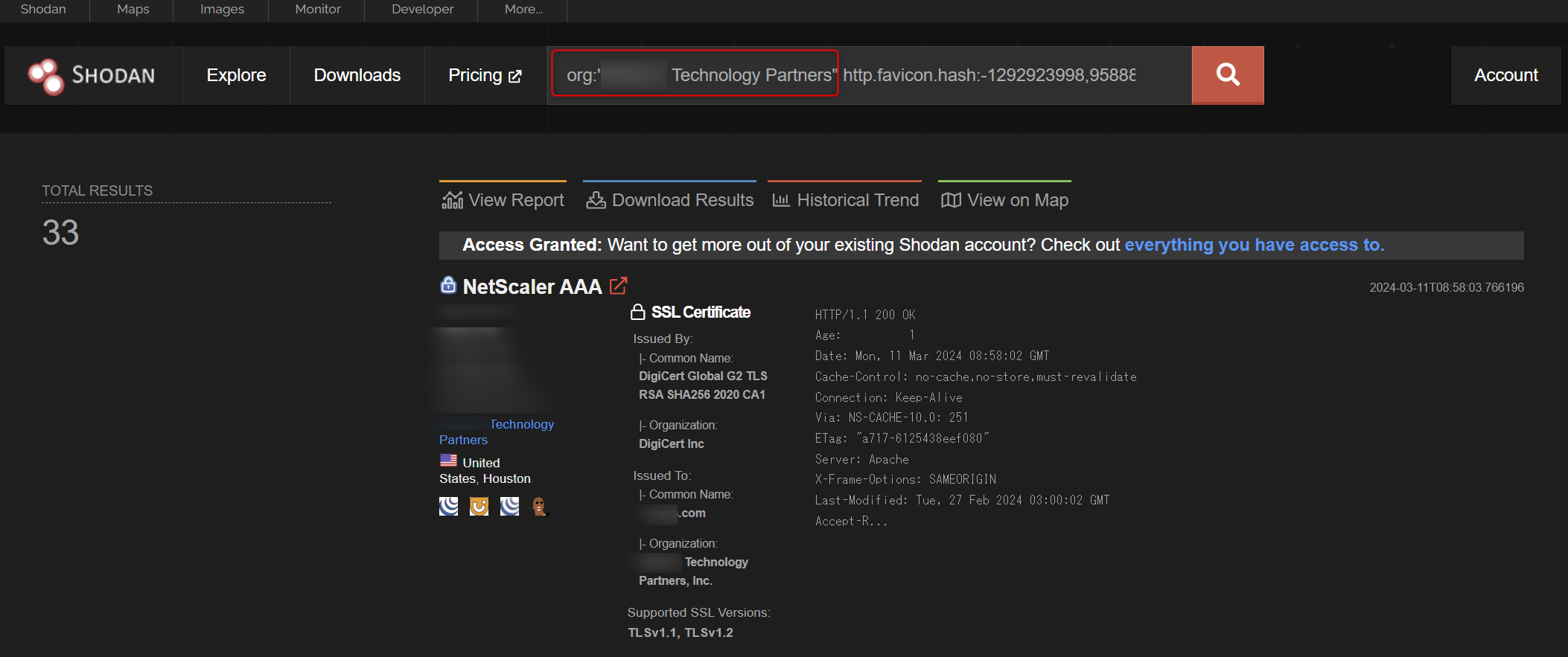
A simple research method can be conducted using Shodan.
Citrix ADC and Gateway can be searched with the following query.
http.title:netscaler,"Citrix&Gateway"
http.favicon.hash:-1292923998,958889263,-1166125415,-1272756243,-614313335
In addition to the above query, by combining the query with ssl:example.com or org:"example company", it is easy to extract the assets of the targeted organization that has been attacked. Enter the domain used by the company under investigation after ssl: and the name of the company under investigation after Org:.
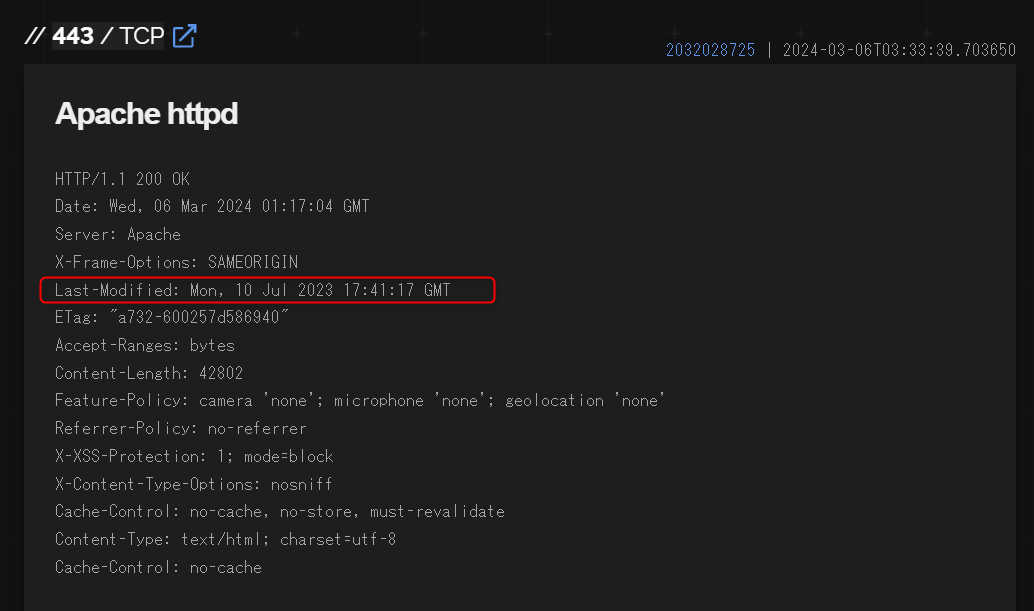
Based on my research, it has been found that Citrix servers with a Last-Modified date in the server response before 2023/9/21 are highly likely to be vulnerable to CVE-2023-4966. Therefore, this criterion is used to determine the presence of the vulnerability.
■The situation of exploitation by ransomware actors
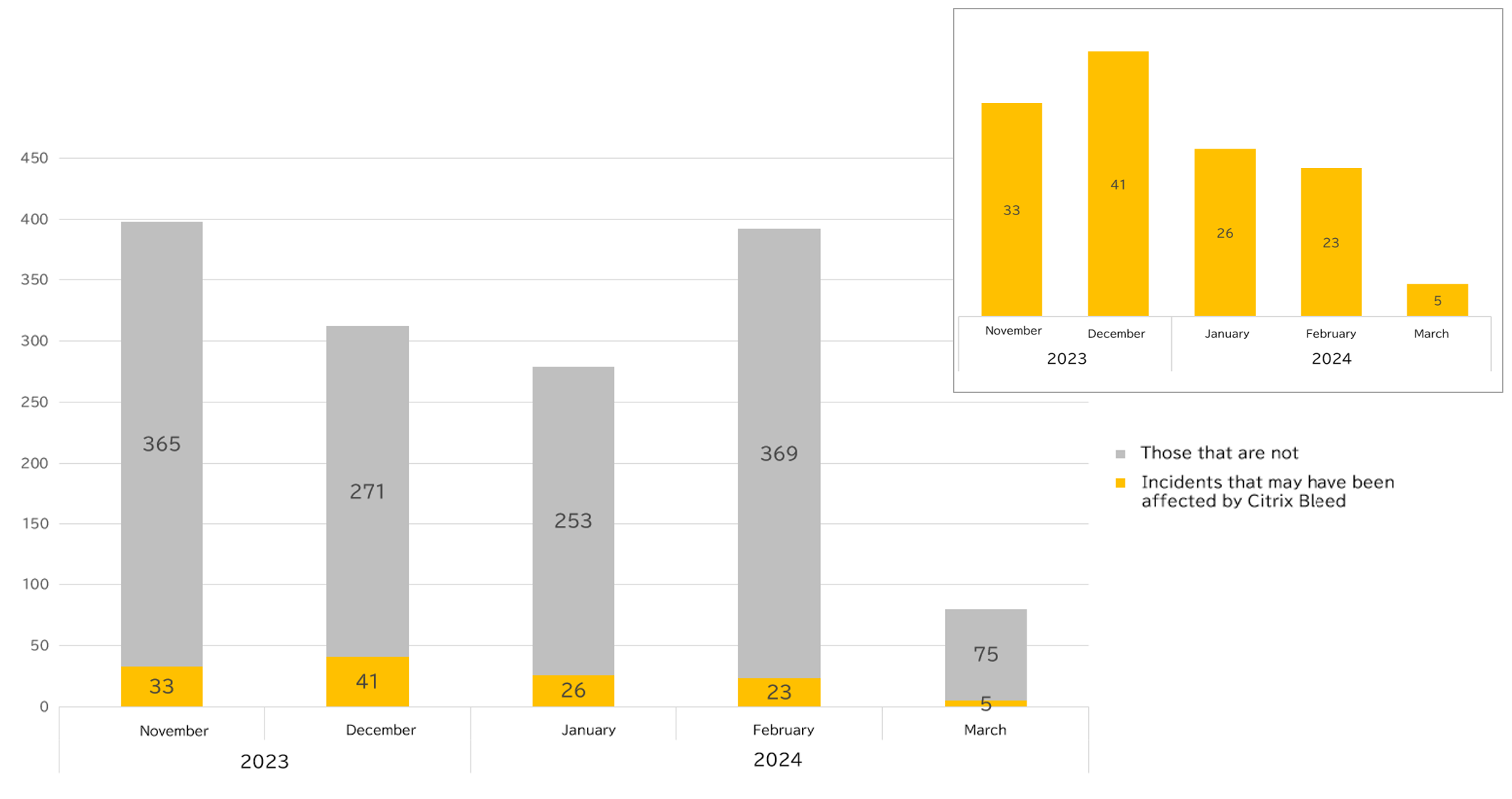
This time, I checked whether companies leaked by ransomware actors from November 2 ,2023 to March 5, 2024, possessed Citrix servers vulnerable to CVE-2023-4966.
During this period, 1,457 leaks from various attackers were identified, and it was found that 128 of these organizations possessed vulnerable Citrix servers. *This figure is the result of a simple investigation, and a more thorough OSINT investigation could potentially reveal more vulnerable Citrix servers.
Counting the incidents monthly shows the following trend: after peaking in December 2023, the number of incidents has been decreasing, but incidents thought to be caused by Citrix Bleed are still occurring.
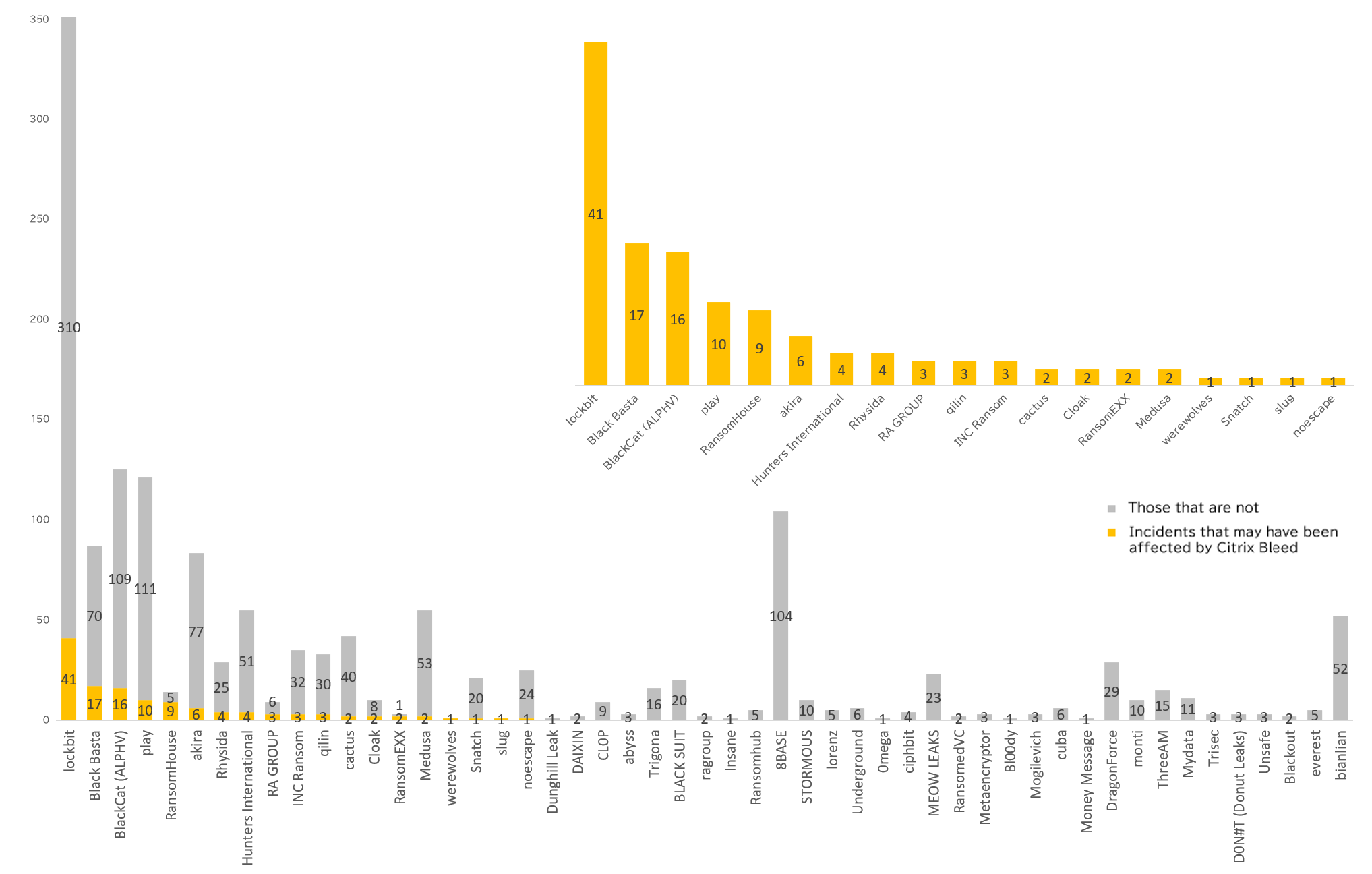
Next is a graph aggregated by each attacker. Attackers (including some of their affiliates) such as Lockbit, Black Basta, Black Cat, Play, and RansomHouse may have actively exploited this vulnerability.
While public interest in Citrix Bleed has almost faded, it seems that attackers are still focused on it.
フォローしませんか?