Additional Evidence of SonicWall CVE-2024-40766 Exploitation by Akira and Fog, and Patch Progress
Introduction
In September 2024, the SonicWall NSA vulnerability CVE-2024-40766 was disclosed. I have found strong indications that the ransomware groups Akira and Fog are still exploiting this vulnerability for unauthorized access. Through my ongoing investigations, I found that, as of December 23, 2024, the number of companies suspected to have been compromised by these two groups via this vulnerability had exceeded 100. In this article, I will share the details of this investigation and highlight the current situation in which at least 48,933 devices remain vulnerable to CVE-2024-40766.
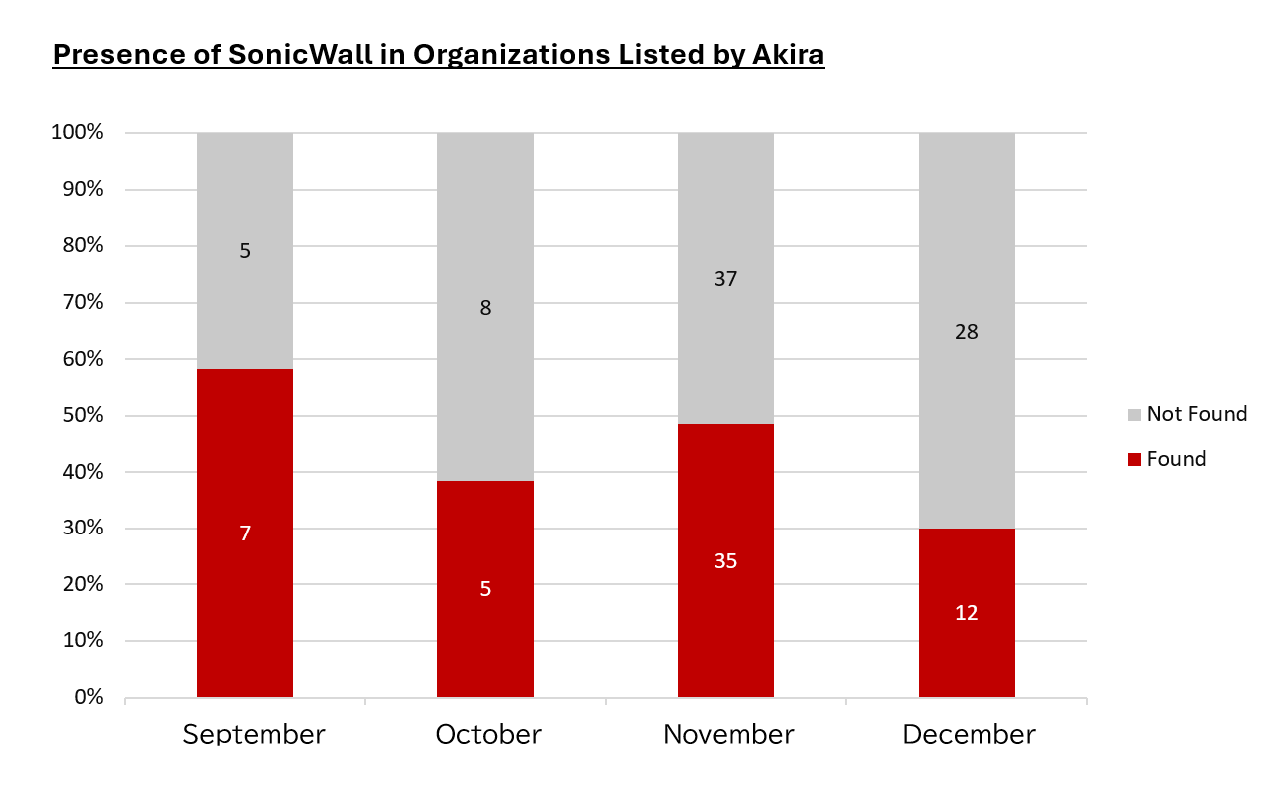
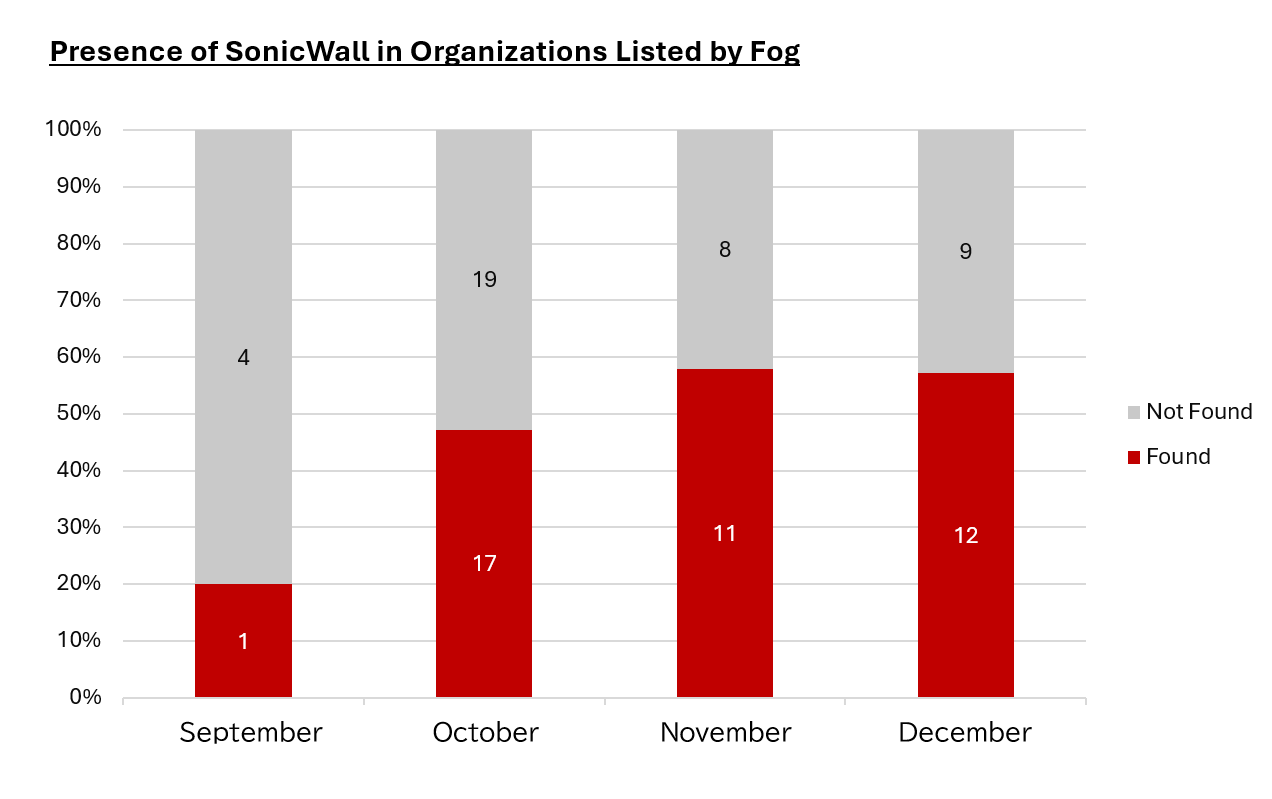
Possible Exploitation by Akira and Fog
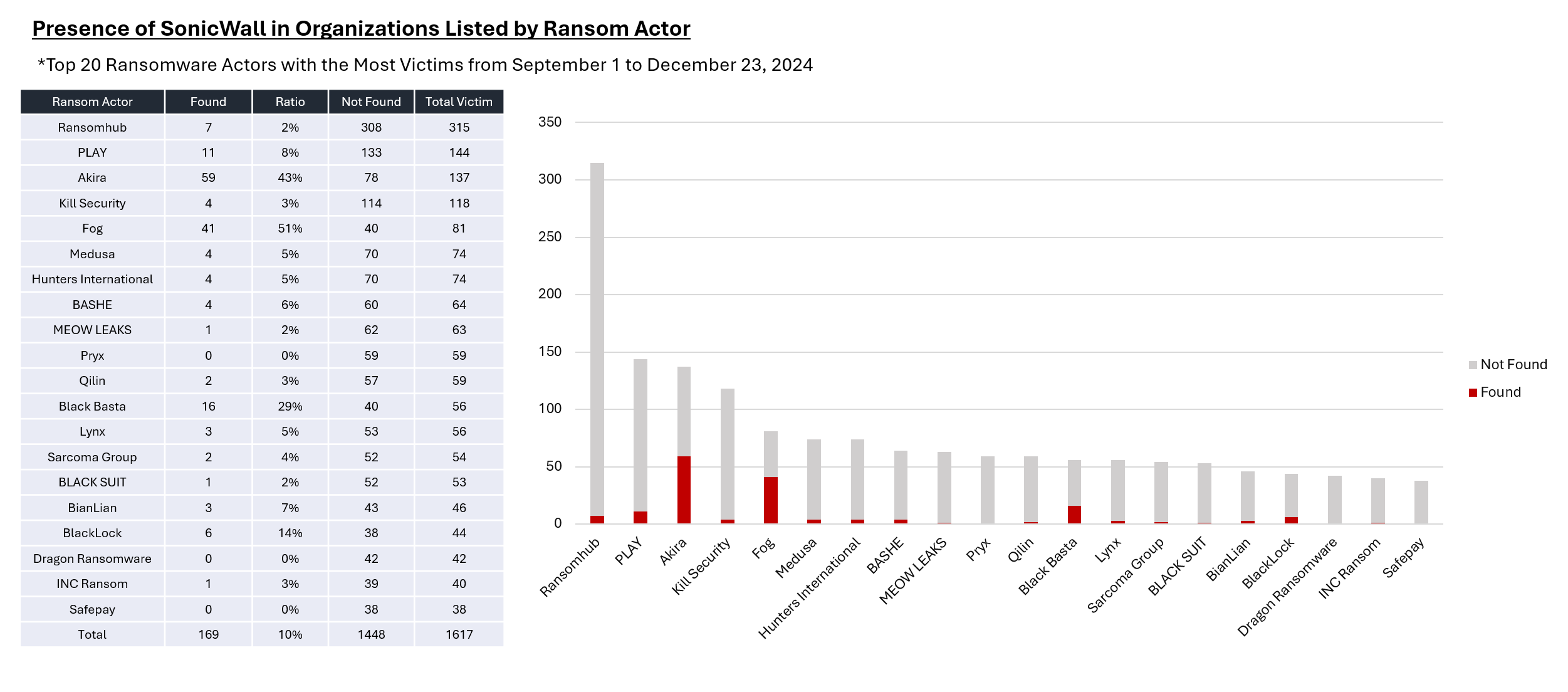
Since the vulnerability was disclosed in September 2024, I have been investigating whether organizations--listed on various ransomware groups' leak sites--own SonicWall NSA devices. Focusing on the 218 organizations identified as victims of Akira and Fog, I found that over 100 (approximately 46%) were actually running SonicWall. Considering that the SonicWall NSA ownership rate among organizations victimized by other ransomware groups (excluding Akira and Fog) remains at around 5% or less, this figure is remarkably high.
This trend has continued from September through December. Depending on the period, this figure can exceed 50%.
Naturally, since many affected companies are not posted on leak sites and there may be cases where I have yet to correlate certain victims with SonicWall, the actual number of compromised organizations could be even higher.
Potential reasons why the detection rate has remained at around 50% include:
- Limitations of the author's investigation: Because it is generally harder to link a company to its SonicWall device than it is for some other products (e.g., Ivanti or Citrix), there is likely a portion of victims that remain undetected.
- Operational strategies of attackers: The attackers might be diversifying their intrusion vectors to avoid drawing too much attention to the SonicWall vulnerability.
- Differences among internal execution groups: Even within the same threat actor group, individual operators may employ different tactics or methods.
While some security vendors who directly handled incidents linked to Akira and Fog have suggested that the SonicWall NSA vulnerability may have been exploited, they have generally refrained from making definitive statements.
https://gblogs.cisco.com/jp/2024/10/talos-akira-ransomware-continues-to-evolve/
The likely reason is the difficulty in determining whether stolen credentials were obtained via this particular vulnerability or through other means, especially if the vulnerability allows for credential theft. SonicWall has not provided sufficient information about the potential impact of the vulnerability when exploited, and no PoC has been publicly released, leaving many details unclear. Nevertheless, SonicWall itself has recommended resetting credentials and implementing multi-factor authentication (MFA), suggesting that this vulnerability could indeed be tied to credential theft.
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2024-0015
Based on the high concentration of SonicWall devices found in organizations targeted by Akira and Fog, I wrote this article in hopes of providing further evidence that these actors are exploiting SonicWall vulnerabilities.
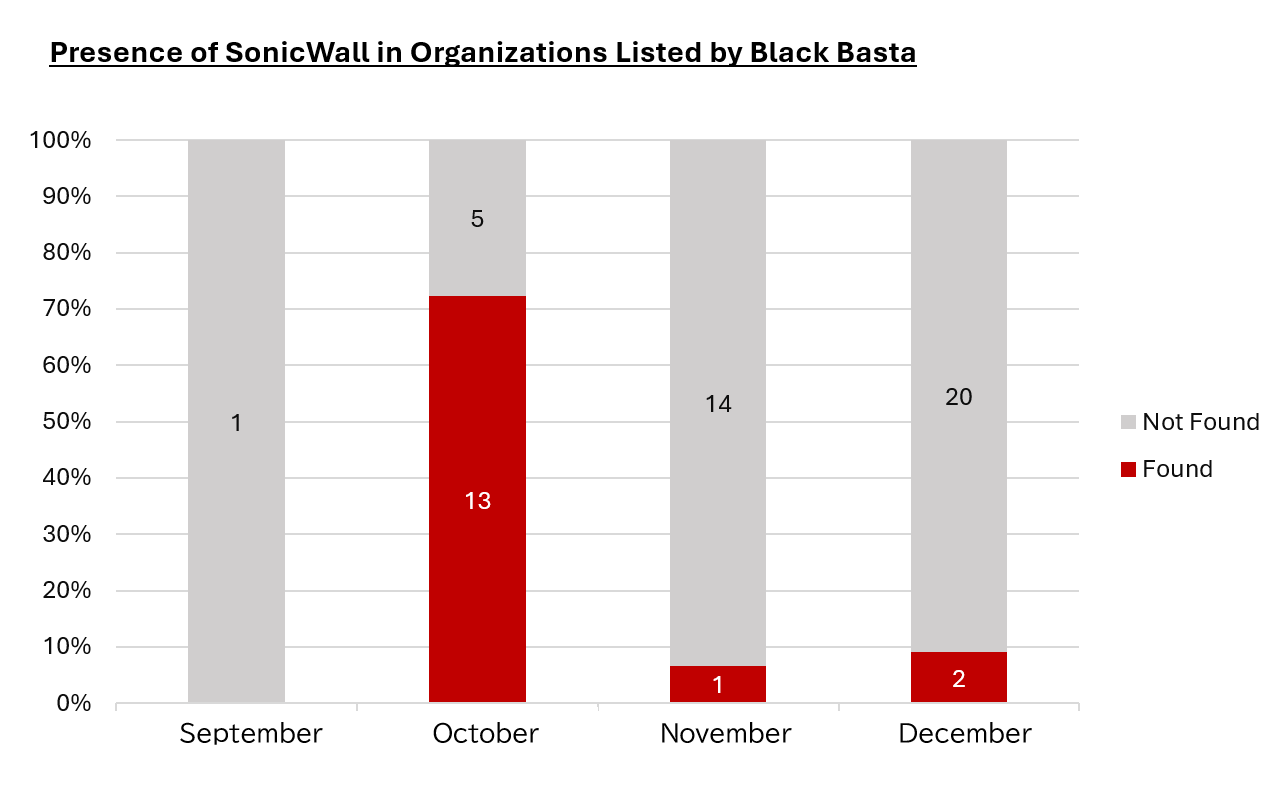
In addition, it is worth noting that there was a period when BlackBasta also appeared to be exploiting SonicWall; however, such activity seems to have subsided recently.
Current Patch Status
I developed a proprietary method to evaluate patch status by examining the HTML structure of SonicWall devices to assess mitigation efforts for CVE-2024-40766. For SonicWall NSA devices with SNMP exposed, it is possible to obtain accurate model and version information. By comparing the results of my custom method with SNMP data from around 5,000 devices, I've confirmed a certain level of accuracy for this detection approach.
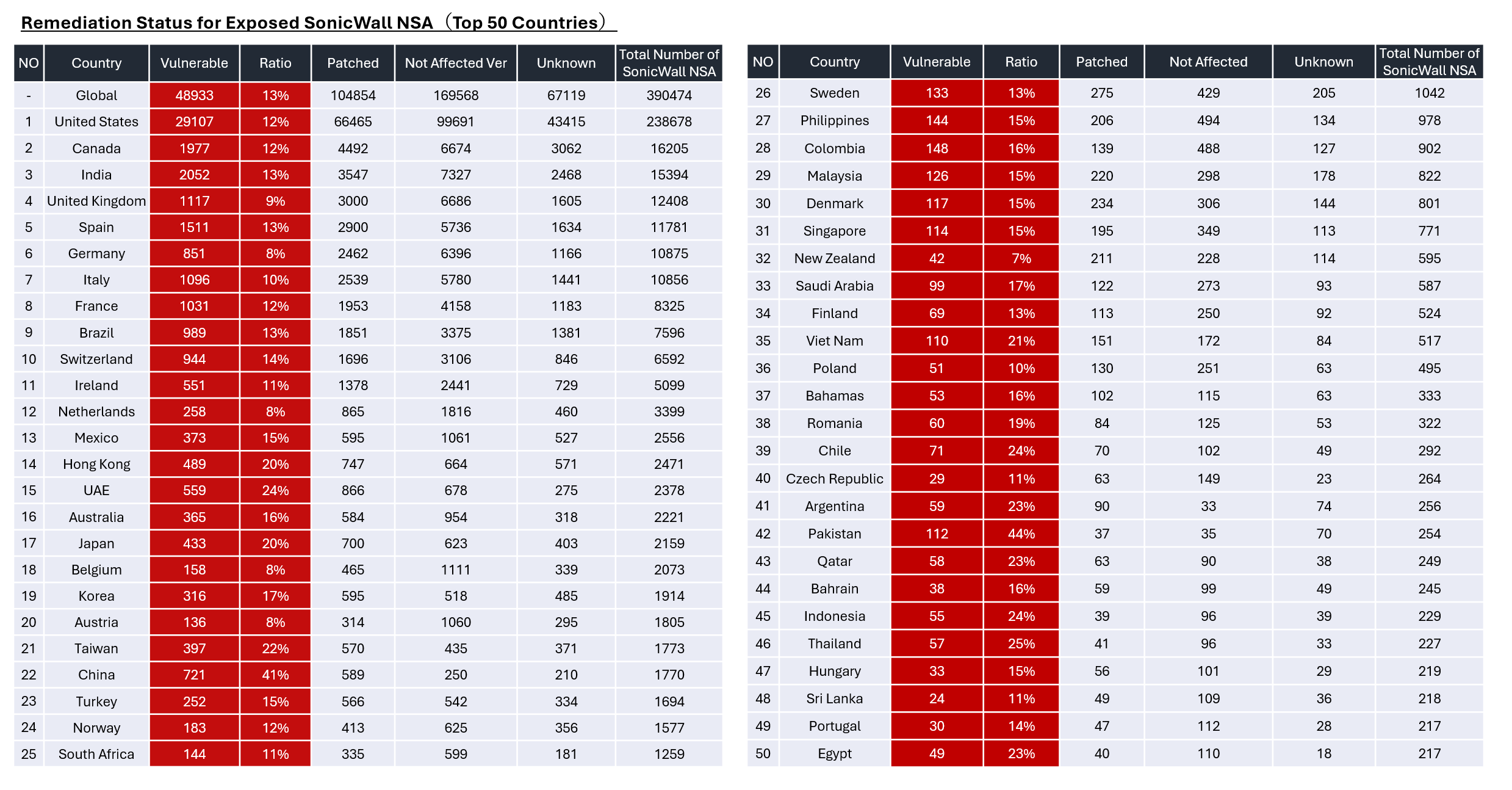
As of December 24, 2024, the results indicate that the following SonicWall NSA devices remain exposed to the internet without the necessary patches. Specifically, at least 48,933 SonicWall devices remain vulnerable.
This graph shows the trend of vulnerable servers among publicly exposed servers by country. I observe poor remediation in several Asian countries and a clear slowdown in patch adoption about a month after release--a pattern common across most vulnerabilities, not just this one.
Summary and Outlook
In summary, this article highlights three key points:
- While no security vendors have definitively claimed that CVE-2024-40766 is being exploited, the circumstances suggest that Akira and Fog are highly likely to be using it.
- Three months after the vulnerability was identified, SonicWall remains a target as of December. The number of victims leaked by Akira and Fog has significantly increased, which may be contributing to their growing success.
- As of now, 13% of global public servers, totaling 48,933, still have not applied patches for the vulnerability. It is expected that victims will continue to emerge.
Thank you for reading. Macnica Security Research Center publishes a wide range of information. Although many of our past articles are in Japanese, please feel free to enjoy them using a translation tool.
https://security.macnica.co.jp/
Future articles written in English will be published at the following URL: